Ludovic Rousseau's blog
My activities related to smart card and Free Software (as in free speech).
Important!
Blog moved to https://blog.apdu.fr/
I moved my blog from https://ludovicrousseau.blogspot.com/ to https://blog.apdu.fr/ . Why? I wanted to move away from Blogger (owne...
Wednesday, September 27, 2023
Wednesday, August 30, 2023
Friday, June 9, 2023
Friday, May 12, 2023
Blog moved to https://blog.apdu.fr/
I moved my blog from https://ludovicrousseau.blogspot.com/ to https://blog.apdu.fr/.
Why?
I wanted to move away from Blogger (owned by Google since 2003) and host the blog myself on a server I control.
Low tech
The blog is now managed by the Nikola Software. I discovered Nikola by reading a Linux Weekly News article Nikola: static-site generation in Python.
Once generated, the HTML pages are static so it is very easy and simple to host them on a web server. No need to have a database (like MySQL) on the server or run a program (like PHP) to generate the content.
Web design
I use the bootstrap4 Nikola theme with some custom changes.
I am not a web page designer. Some colors or styles may look ugly. Please send me CSS change suggestions.
Update your bookmarks
If you have links pointing to the old blog it is very easy to update them to use the new blog.
For example, you have a link to https://ludovicrousseau.blogspot.com/2021/10/what-happened-20-years-ago.html. The same article is now available at https://blog.apdu.fr/posts/2021/10/what-happened-20-years-ago/
replace "https://ludovicrousseau.blogspot.com/" by "https://blog.apdu.fr/posts/"
replace ".html" by "/"
It looks magic, but it works because I used the Nikola plugin
import_blogger to
import all the articles from Blogger. I then made some "manual" corrections.
Update your RSS feed
To automatically receive new articles you can register your news reader to the RSS feed at https://blog.apdu.fr/rss.xml.
Conclusion
I already updated the links I have on my other web pages to point to the new blog.
I do not plan to close the old blog at Blogger because a lot of other pages still point to it. And it is very annoying to get an HTTP 404 error when you are redirected to a web page that does not exist anymore.
Sunday, April 23, 2023
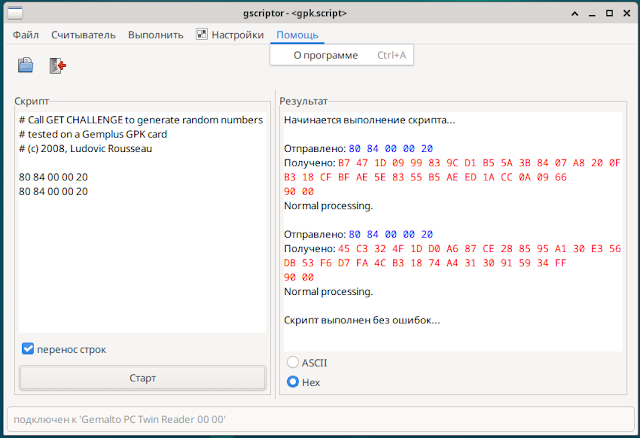
gscriptor now also in French and Russian
I modified gscriptor (included in pcsc-tools) to support internationalization (i18n). The next version of gscriptor (no release date planned yet) will be available (at least) in French and in Russian.
gscriptor
gscriptor is a graphical tool to send APDU commands to a smart card.

|
It is written in Perl and uses the Gtk+ graphical library.
French
Russian
Conclusion
Thanks to Pro-pra for the initial patch and the Russian localization.
If you want to add another language please copy the file
pcsc-tools.pot, add your translations and send me the resulting file.
Sunday, April 16, 2023
FAQ: pcsc-lite and SCARD_E_SERVICE_STOPPED error
One of the most popular search request that bring people on my blog is about
SCARD_E_SERVICE_STOPPED.
The problem
With pcsc-lite the only cause for the error
SCARD_E_SERVICE_STOPPED is that the two sides, pcscd and
libpcsclite, are using a different version of the communication protocol.
See for example the reported issue "SCardEstablishContext: Service was stopped.".
In the logs you have something like:
$ journalctl --unit=pcscd [...] févr. 11 18:55:07 debian pcscd[3715]: 00000006 winscard_svc.c:361:ContextThread() Received command: CMD_VERSION from client 8 févr. 11 18:55:07 debian pcscd[3715]: 00000004 winscard_svc.c:373:ContextThread() Client is protocol version 4:3 févr. 11 18:55:07 debian pcscd[3715]: 00000001 winscard_svc.c:382:ContextThread() Communication protocol mismatch! févr. 11 18:55:07 debian pcscd[3715]: 00000002 winscard_svc.c:384:ContextThread() Client protocol is 4:3 févr. 11 18:55:07 debian pcscd[3715]: 00000001 winscard_svc.c:386:ContextThread() Server protocol is 4:4 févr. 11 18:55:07 debian pcscd[3715]: 00000002 winscard_svc.c:396:ContextThread() CMD_VERSION rv=0x8010001E for client 8Here the server is using version 4.4 but the client is using version 4.3.
The error code
0x8010001E is
SCARD_E_SERVICE_STOPPED.
The cause
This situation can happen if you reinstalled pcsc-lite yourself but in
You may also use an application inside a flatpak container that uses a different version of pcsc-lite. See the limitations listed in "Accessing smart cards from inside a flatpak sandbox".
The solution
Do not mix different versions of pcsc-lite.
Conclusion
This is the second article in the FAQ "section". The first one was "FAQ: wintypes.h or winscard.h not found". I will try to provide other articles about common errors.
Friday, April 14, 2023
Verify with OpenSSL a signature computed by PyKCS11
With PyKCS11 I provide a sample code signature.py to compute a RSA+SHA256 signature. The Python sample also contains the code to check the signature using PyKCS11.
But what if you want to verify the signature using OpenSSL?
Export the public key
$ export PYKCS11LIB=/usr/local/lib/softhsm/libsofthsm2.so
#!/bin/bash
set -e
# get the 1st key object ID
ID=$(pkcs11-tool --module $PYKCS11LIB --list-objects --type pubkey \
| grep ID \
| cut -d: -f 2)
echo "Object id: $ID"
# export the public key
pkcs11-tool --module $PYKCS11LIB --read-object --type pubkey --id $ID -o rsa_pub.key
# convert the public key to PEM
openssl rsa -pubin -inform DER -in rsa_pub.key -outform PEM -out rsa_pub.pem
The RSA key pair has been generated by the
generate.py
script and is stored in the PKCS#11 token. We need to export it so that
OpenSSL can use it to check the signature.
To export the key I use pkcs11-tool from the OpenSC project. We need to know the object ID of the public key. This ID is configured in generate.py script line 22. We dump the public keys and get the object ID.
$ pkcs11-tool --module $PYKCS11LIB --list-objects --type pubkey
Using slot 0 with a present token (0x27ca3aa)
Public Key Object; RSA 1024 bits
label: My Public Key
ID: 22
Usage: encrypt, verify, wrap
Access: local
The script will work correctly if only one public key is present in the token. I let you handle more complex cases.
output
$ ./export_key.sh Using slot 0 with a present token (0x27ca3aa) Object id: 22 Using slot 0 with a present token (0x27ca3aa) writing RSA key
Compute signature
#!/usr/bin/env python3
from PyKCS11 import *
import binascii
pkcs11 = PyKCS11Lib()
pkcs11.load() # define environment variable PYKCS11LIB=YourPKCS11Lib
# get 1st slot
slot = pkcs11.getSlotList(tokenPresent=True)[0]
session = pkcs11.openSession(slot, CKF_SERIAL_SESSION | CKF_RW_SESSION)
session.login("1234")
# message to sign
toSign = "Hello World!\n"
mechanism = Mechanism(CKM_SHA256_RSA_PKCS, None)
# find first private key and compute signature
privKey = session.findObjects([(CKA_CLASS, CKO_PRIVATE_KEY)])[0]
signature = session.sign(privKey, toSign, mechanism)
print("\nsignature: {}".format(binascii.hexlify(bytearray(signature))))
# save the clear text in a file
with open("cleartext.txt", "w") as f:
f.write(toSign)
# save to a signature in a file
with open("sig_sha256.bin", "bw") as f:
f.write(bytearray(signature))
# find first public key and verify signature
pubKey = session.findObjects([(CKA_CLASS, CKO_PUBLIC_KEY)])[0]
result = session.verify(pubKey, toSign, signature, mechanism)
print("\nVerified:", result)
# logout
session.logout()
session.closeSession()
Output
$ ./signature.py signature: b'322c1591cb9aba1e361264b02464a2bd9d55693bf772b4253da0862616e611dc139005742c511795c27c8f609e4ddbaafceba1c3b3ce278b8e0af564c84de54a639cff67a9a3f97dcc542cd6f0200954ef7fce4a0f87b61636272e21fc1e3ef9f0b683e360cca4231405dd90ae2c4a3638ca7a85e2b62f6ae30975ff3885ab60' Verified: True
Verify signature
#!/bin/bash set -e # verify signature openssl dgst -sha256 -verify rsa_pub.pem -signature sig_sha256.bin cleartext.txt
Output
$ ./verify.sh Verified OK
Conclusion
Thanks to Leon Rman for the initial code and the idea.
I let you write the code to do the symmetrical operations: sign using OpenSSL and verify using PyKCS11.